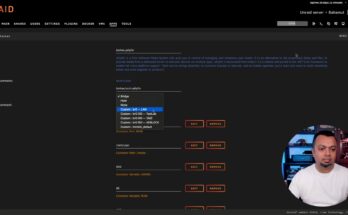
Use VLANs for docker containers on Unraid
Unraid makes it very easy and intuitive to use VLANs for your docker containers. In this video I will show you how to add them and then how to use them when creating a docker container.
Pragmatic IT Solutions

Unraid makes it very easy and intuitive to use VLANs for your docker containers. In this video I will show you how to add them and then how to use them when creating a docker container.
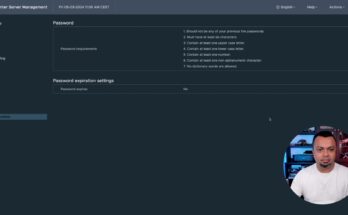
Here is how you can change the password policy (call it complexity) for user accounts on VMware vCenter 8. You can adjust the password expiration time, or disable it completely if you need to.
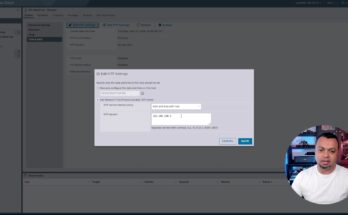
In this video, I will show you how to configure NTP Time Service centrally for vSphere 8 and vCenter 8 in your network. This is one of the first steps you need to take when setting up a VMware environment.
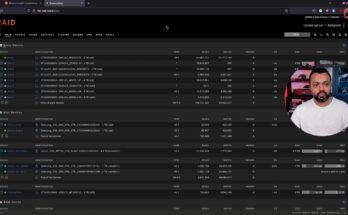
In this video, I show you how the Array Devices and several Pool Devices can be used on Unraid server.
More info on Unraid Array and Pool Devices can be found here.
Unraid Array Devices and Pool Devices explained Read More
In this video, I will talk about my next journey for personal NAS storage and what aspects I have considered in choosing another personal NAS storage solution and building my own personal cloud.
Reading Time: < 1 minuteIn this video, I will show you how to add custom domains to block when using pfBlockerNG and pfSense to keep away ads and tracking on your network. After all, what you do on the internet is nobody’s business.
Adding custom domains to block with pfBlockerNG and pfSense Read More